Why Is Network File System (NFS) Insecure?
NFS relies entirely on essentially insecure UDP protocol (sends datagram instead of client-server connection), makes unencrypted transactions, and lacks definite user authentication.
Most of our societies insist on the power and significance of sharing. This motive led to the establishment of the Network File System (NFS). NFS has always been bound to change versions. The current standards like NFSv4 and NFSv4.1 are likely to perform poorly when data traffic increases.
This is what Ardash Chetan on LinkedIn had to say concerning NFS security, “NFSv4 designed to work on the internet. One of the main reasons to design NFSv4 was to provide strong security, with negotiation built into the protocol. The main security in V4 is mandatory Kerberos support and improvement in username/UID management. NFSv4 provides all security capabilities such as Server authentication, Client authentication, User Authentication, Data integrity, Data confidentiality.”
NFS communication is based on request-response protocol (RPC). RPCs are essentially insecure unless performed in a firewalled network. These v4s also have restricted scalability and bandwidth.
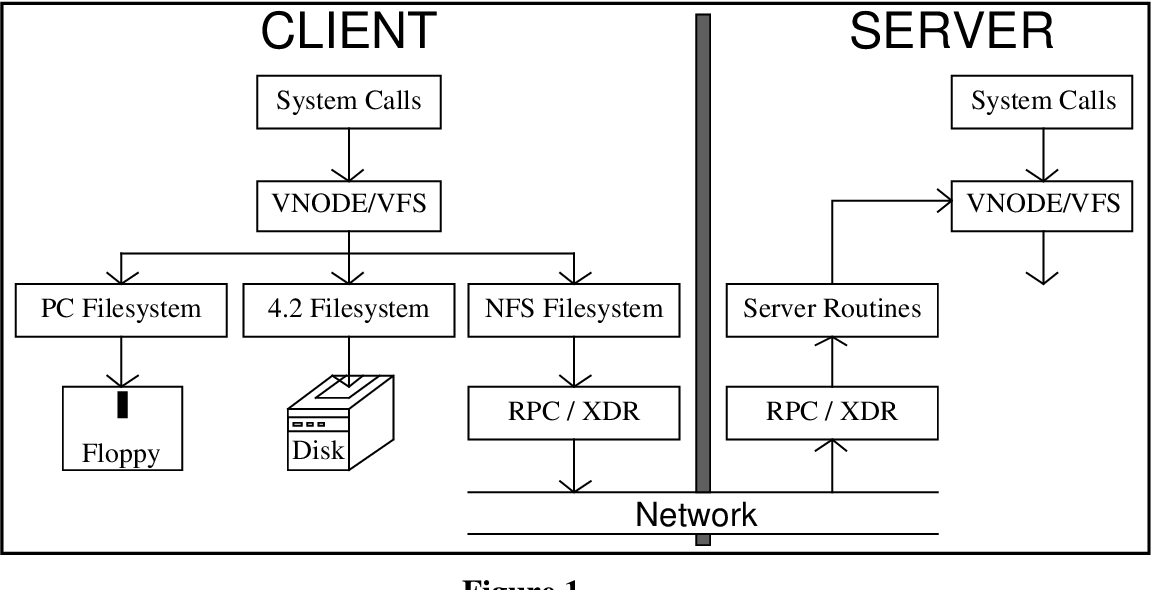
Before diving into how and why NFS is insecure, at least you should understand how it works. NFS is a primitive client/server protocol for remote file sharing, like Telnet. It allows the client computer to view, store, and update remote server files as though they were stored locally.
Communication occurs based on mount commands, with attributes and options, made in the server. The current versions are NFSv3, NFSv4, and NFSv4.1.
In this post, you will learn why and how NFS is insecure, and some NFS security best practices.
NFS security issues
The lack of sophisticated encryption capabilities renders NFS vulnerable to cyberattacks. Any smart intruder can easily intercept and read your data in transit.
An eavesdropper gains unauthorized access to your data before reaching the host. An impostor will gain unauthorized access to the network.
Your NFS server cannot differentiate between daemon mountd filehandles and falsified ones. An attacker can configure its client computer to snoop the connection and make away with a filehandle, read and alter a server file the root does not own.
As aforementioned, NFS uses RPCs to communicate, such that client/server communication does not happen vice versa. NFS file system exports occur locally- hosts have a particular mount point. The mountd daemon enforces the host list. Isn’t that a threatening vulnerability?
An attacker client may access the corresponding server portmap daemon to execute a mountd daemon request. The mountd will perceive the request as valid and obeys the command.
If you unrestrictedly export a file system, an attacker can remotely tamper with your file or the system files. The intruder wins and takes full control over your computer.
By default, the UNIX numeric groupid and userid (AUTH_UNIX) specifies your authentic identity for accessing a directory or a remote file. It’s simple for any user to execute a program that generates a request to obtain file access for any user.
These security issues exist, but why do some of you still use this file sharing protocol?
You should probably understand the following general ways of securing NFS to minimize the insecurities.
NFS security best practices
- Install the latest software application patches. If you don’t have patches that address security matters, you will have given an attacker a run for their bucks and time. NFSv4 version has specific security mechanism improvements. It supports Kerberos 5 data protection and authentication to support the preexisting AUTH_SYS security. This security feature saves for future security mechanisms addition.
- Configure your NFS server to export the file systems with the least necessary privileges. Use SMIT or the /etc/exports file editing to specify your file privileges. If you want to only read from your file system, you should not write to it. So an attacker cannot overwrite data, alter config files, or even code executable bugs to your exported file system.
- Configure your NFS server to categorically export file systems for your allowed users. NFS will enable you to specify clients who access a particular file system. This will discourage unauthorized file systems access.
- Partition individual exported file systems. In the case of a system degradation attack, the attacker cannot write an exported file system. If they manage to write until it’s complete, your other applications and users cannot avail the file systems.
- Configure your NFS implementations to map unknown or privileged to unprivileged user requests. The NFS clients will not allow file system access with root/ unknown user details. An attacker will not act/ operate as a privileged user to access the file system.
- Embrace Secure NFS. Secure NFS uses Data Encryption Standards (DES) for authenticating RPC transactions hosts. Secure NFS encrypts the RPC time stamp requests; hence an attacker cannot spoof them. The receiving end decrypts the time stamp and confirms the authenticity of the RPC requests.
Does NFS have authentication?
NFS uses DES algorithms to encrypt a timestamp in RPC transactions. The timestamp then authenticates your computers the moment the token does sender authentication.
Each file system is secured additionally and optionally because NFS authenticates all RPC transactions. You can easily specify a secure file system export option. It’s possible because file systems are exported with the standard UNIX authentication by default.
Does NFS use TLS?
NFS host connections are clear-text by default, making them incompatible with sensitive data. Transport Layer Security (TLS) can cover this protocol data security.
TLS 1.2 encrypts NFS traffic in transit when your file system is mounted. An industry-standard AES-256 cipher cryptographic element is responsible for this encryption.
Every file system that a client accesses in transit should have encryption.
Conclusion: Is NFS secure?
NFS is vulnerable to most streaming internet attacks. It is a primitive transfer protocol used for remote file sharing. Its use diminished as more secure and advanced technology transfer protocols were established.
NFS authenticates data handling through DES algorithms that encrypt RPC transactions. NFS lacks definite encryption mechanisms unless used with TLS. The latest version, NFSv4.1, has a relatively less susceptible level of security. If you can carefully configure specific settings and features, NFS can still serve your remote file sharing tasks.
